What Happened
In 2017, one of our clients suffered a Distributed Denial of Service (DDoS) attack that briefly knocked their public website offline. The attack originated from thousands of devices, likely a botnet of compromised home PCs distributed across different networks. It was carefully structured to avoid detection, using constantly rotating IP addresses.
The traffic pattern pointed to Asia, a legitimate market for the client’s business. This ruled out blunt geoblocking as a viable mitigation method.
Proactive Detection
Thanks to Taurix IT’s active monitoring systems, the attack was detected in real time. This allowed us to launch an immediate response before any lasting damage was done.
Our Response
We quickly implemented a two-part mitigation strategy:
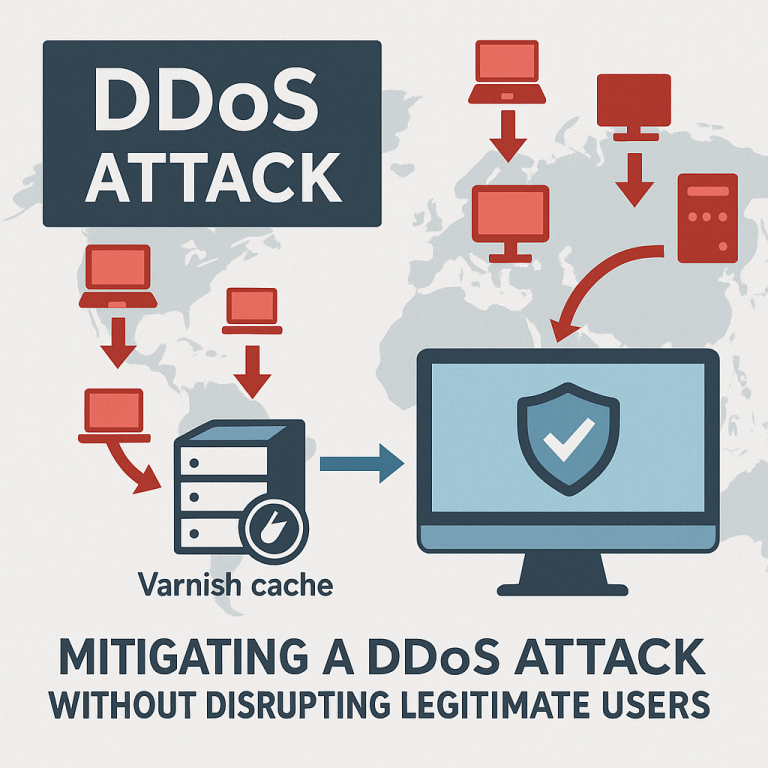
- Targeted Redirection and Filtering
The attack focused on a single URL with account-related functionality. Blocking this path directly was not enough to reduce server load or protect users. Instead, we deployed an additional Varnish caching server and redirected all Asian traffic to this new node. There, we blocked the targeted URL with an in-memory rule, neutralizing the attack without affecting access to the rest of the site. - Preserving Service for Real Users
The backend shop was isolated from the attack and only received legitimate traffic. As a result, it remained completely unaffected. The public site continued to serve real users with no noticeable performance degradation.
The Outcome
- The website remained online and responsive
- Malicious traffic was isolated and neutralized
- No service disruption to legitimate users
- The backend store remained fully operational
- No ransom was paid or negotiated
- The client avoided business interruption or reputational harm
Why It Matters
This case shows how proactive monitoring and layered infrastructure can turn a potentially crippling DDoS event into a non-issue. Taurix IT delivers not just hosting, but real-time protection, response, and resilience — even when traditional defenses fail.

